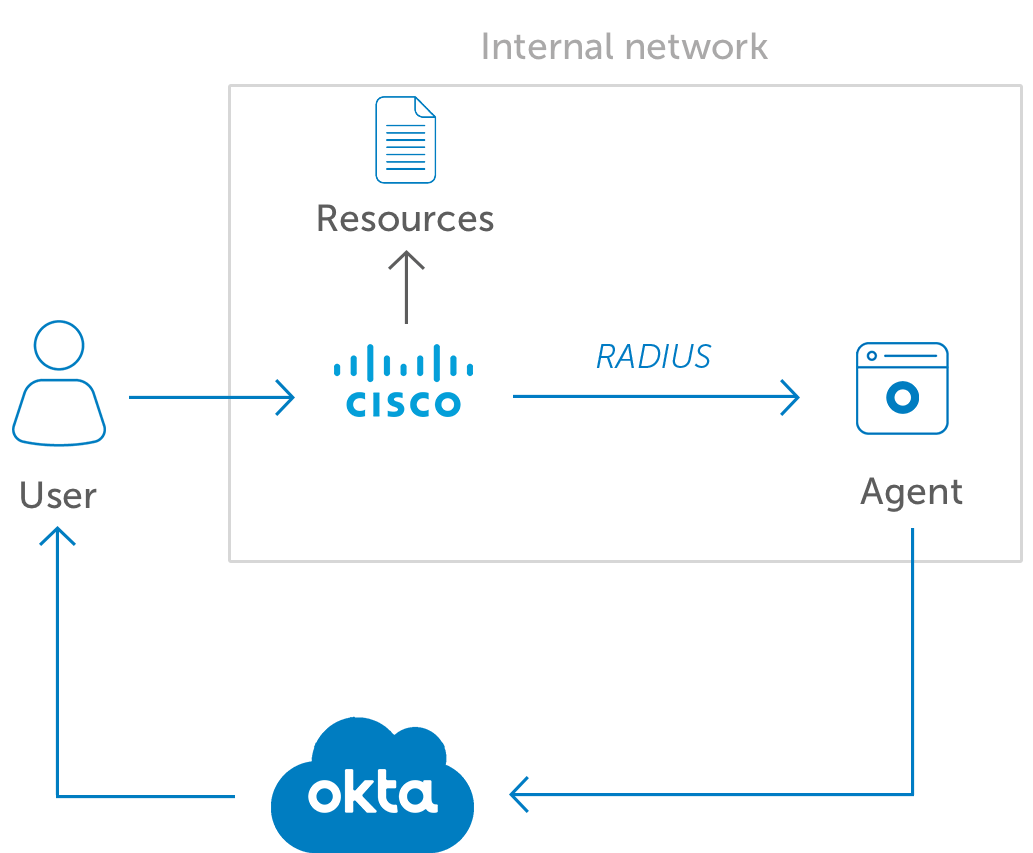
Okta provides secure access to your Cisco VPNs by enabling strong authentication with Adaptive Multi-Factor Authentication (MFA). Our MFA integration supports Cisco ASA VPN and Cisco AnyConnect clients using the Okta RADIUS server agent. Okta’s app integration model also makes deployment a breeze for admins.
About Okta Mobility Management
- Okta released a special COVID-19 edition of its app usage report today, and you don’t need a Ph. In statistics to guess what they found. Indeed, Zoom surged 110% on the Okta network, leading.
- Select the Juniper SSL VPN option. Support Announcement: Apple no longer supports Juniper VPN options on macOS Sierra.This is an Apple limitation. Okta will maintain this option, but will not support it with bug fixes.
- Apr 30, 2020 The biggest winners here beyond collaboration tools were VPN businesses with Palo Alto Networks GlobalProtect and Cisco AnyConnect coming in at 94% and 86% usage increases respectively.
- The OMM menu is available only to orgs that implement Okta Mobility Management (OMM).
- Operations documented in this article are available only to customers who have already purchased OMM for their organization. New OMM sales are not supported. For more information, contact Okta Support.
This is an Early Access feature. To enable it, please contact Okta Support.
Okta Mobility Management (OMM) can provision password-based, device-wide VPN configurations directly to devices without requiring IT to duplicate infrastructures or implement application proxies and gateways. Okta uses the native VPN capabilities built into the mobile operating system to leverage existing VPN solutions and enable easy access to on-premises resources. Notes:.
- The OMM menu is available only to orgs that implement Okta Mobility Management (OMM).
- Currently, this feature is available only for iOS devices.
- Go to OMM > VPN.
- Click Add Device VPN.
- Select a VPN client.
Support Announcement: Apple no longer supports PPTP or Juniper VPN options. This is an Apple limitation.
- Configure your VPN client as described in one of the following procedures:Configuring Cisco AnyConnect
- Under General Settings, consider the following:
- Application Label: The label displayed under the app on your home page. By default this is Cisco AnyConnect VPN.
- VPN Server: Enter the IP address or hostname of your VPN server. If you are using ipsec, you must specify the corresponding protocol. For example: ipsec://asa-gateway.example.com.
- Click Next.
- Under Sign-On Options:
- VPN Password: Select either:
- Delegated Authentication: Select this option if your company VPN is configured to authenticate with Active Directory and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your AD credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users' devices.
- Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with the Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
- Advanced Sign-On Settings. Optional.
- Group for authenticating connection: Specify the group policy name.
- Make sure you add a Group URL in Cisco AnyConnect settings that corresponds to the ASA server and group you use.
- If you are using Cisco ASDM utility, you can do this under Connection Profiles > Your group > Advanced settings > Group Alias/Group URL. For example: ipsec://asa-gateway.example/com/group1
- VPN Username.
- VPN username format: Use the drop-down menu to select a format.
- Password reveal: Check this if you want your users to securely see their password.
- This is how we determine what username to use in the VPN profile, this function the same way as the username mappings in other non VPN applications.
- Group for authenticating connection: Specify the group policy name.
- Click Done.
- In the People tab, assign your app to users and groups. You also need to make the app available to your end users via the Okta Mobile App Store (Android and iOS). To do so:
- Click to the Mobile tab.
- Click the Edit (pencil) icon and select the following:
- Prompt users to install the app on enrollment (iOS 7+)
- If a user already has the app, enable them to make it a managed app from the company app store (iOS 9+)
- Make this app available to users
Configuring Juniper SSL VPN- Select the Juniper SSL VPN option.
Support Announcement: Apple no longer supports Juniper VPN options on macOS Sierra. This is an Apple limitation. Okta will maintain this option, but will not support it with bug fixes.
- Under General Settings:
- Application Label: The label displayed under the app on your home page. By default this is populated by Juniper SSL VPN.
- Server: Enter the IP address of the Juniper VPN server.
- Click Next.
- Under Sign-On Options:
- VPN Password: Select either:
- Delegated Authentication: This setting is to be used if your company VPN is configured to authenticate with Active Directory and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your AD credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users devices.
- Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
- Advanced Sign-On Settings. Optional.
- Realm: Specify a realm for authenticating the connection.
- Role: Specify a role for authenticating the connection.
- RADIUS Authentication Behavior: Retaining this default button allows Okta to perform primary authentication.
- RADIUS Client
- UDP Port: Each RADIUS app has a unique number. Enter it in this required field.
- Secret Key: In this required field, enter the secret key that will be used to encrypt and decrypt the user password. This key must be identical to what is configured on the VPN server.
- VPN Username
- VPN username format: Use the drop-down menu to select a format.
- Password reveal: Check this if you want your users to securely see their password.
This allows Okta to determine which username to use in the VPN profile. This functions the same way as the username mappings in other non-VPN applications.
- Click Done.
This new, configured Juniper SSL VPN client now appears on the Device VPN page. Note that it is activated automatically.
Configuring L2TP VPN- Select the L2TP VPN option.
Support Announcement: Please note that Apple no longer supports PPTP. This is an Apple limitation.
- Under General Settings:
- Application Label: This is the label displayed under the app on your home page.
- Server: Enter the IP address or hostname of your VPN server. If you are using ipsec, the corresponding protocol must be specified, for example: ipsec://asa-gateway.example.com.
- Click Next.
- Sign-On Options. Here you choose how users sign in to the VPN. They can either use a password or they can sign in using Delegated Authentication if it is configured:
Advanced Sign On Settings:
- Shared Secret (L2TP only): Enter a shared secret key for VPN login.
VPN Password: Select either:
Delegated Authentication: This setting is to be used if your company VPN is set up to authenticate with Active Directory, and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your active directory credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users devices.
Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
VPN Username.
- VPN username format: Use the dropdown menu to select a format. This is how we determine what username to use in the VPN profile, this function the same way as the username mappings in other non-VPN applications.
- Password Reveal: Check this if you want your users to securely see their password.
- Click Done.
Configuring Pulse Secure- Select the Pulse Secure VPN option. The Pulse Secure VPN configuration page opens.
- Under General Settings:
- Application Label: This is the label displayed under the app on your home page. By default this is populated by Pulse Secure VPN, but you can edit it if you wish.
- Server: Enter the IP address of the Pulse Secure VPN server.
Click Next.
- Under Sign-On Options:
- VPN Password: Select either:
- Delegated Authentication: This setting is to be used if your company VPN is set up to authenticate with Active Directory, and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your AD credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users devices.
- Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
- Advanced Sign-On Settings. Optional.
- Realm: Specify a realm for authenticating the connection.
- Role: Specify a role for authenticating the connection.
This is how we determine what username to use in the VPN profile, this functions the same way as the username mappings in other non-VPN applications.
- VPN Username
- VPN username format: Use the dropdown menu to select a format. This is how we determine what username to use in the VPN profile, this function the same way as the username mappings in other non-VPN applications.
- Password Reveal: Check this if you want your users to securely see their password.
- Click Done.
In the People tab, assign your app to users and groups.
You will also need to make the app available to your end users via the Okta Mobile App Store. (Android and iOS). To do so
- Click to the Mobile tab.
- Click Edit and complete the following:
- Prompt end users who have already installed an iOS mobile app on their own to allow their admin to manage the app. (iOS only)
- Prompt users to install the app on enrollment. (iOS only)
- Deploy: Click the Make this app available to users check box.
- Under General Settings, consider the following:
Once VPN configurations (profiles) and the respective VPN mobile apps are pushed to OMM-enrolled devices, users can sign in to VPN and work remotely.
Note: The way that VPN profiles are pushed depends on the VPN password settings you configured above:
- Delegated Authentication: VPN profiles are pushed when users are enrolled.
- User sets password: VPN profiles are pushed when users are enrolled, an app user is assigned, or a VPN app instance setting is changed.
- Password is same as Okta: VPN profiles are pushed when the user logs on.
To collect logs from the Okta platform, if you are not using the Sumo Logic FedRamp deployment, use the new Cloud to Cloud Integration for Okta to create the source and use the same source category while installing the app.
The sections below are deprecated for non-FedRamp Sumo Logic deployments. If you are using the Sumo Logic FedRamp deployment, use the sections below to configure collection for this app.This page provides instructions for setting up alog collection from Okta. Click a link to jump to a topic:
Requirements and process overview (DEPRECATED)
Before you begin setting up log collection, review the required prerequisites and process overview described in the following sections.
Prerequisites
- The integration between Sumo and Okta relies upon SumoJanus, a proprietary library used for script-based collection from applications such as Okta, Box, and Salesforce.
- The system where you deploy SumoJanus and configure your installed collector and script source must have Java.
JAVA_HOME environment or absolute PATH variable.Process Overview (DEPRECATED)
Setting up log collection from Okta for analysis in Sumo Logic includes the following tasks, which must be performed in the order in which they are presented.
- Generate an Authentication Token in Okta.
- Download the SumoJanus package necessary for authentication.
- Deploy the SumoJanus package on a local server running the Sumo Logic Collector.
- Edit the local properties file with the Okta token created in step 1. The Properties file will be generated in step 2 when you download and deploy the SumoJanus package.
- Configure an Installed Collector and
- Configure a Script Source in Sumo Logic to send the data from Okta to Sumo Logic.
Configuring Okta log collection (DEPRECATED)
This section walks you through the process of setting up log collection from Okta for analysis in Sumo Logic. Click a link to jump to a topic.
Step 1: Generate the Okta API token (DEPRECATED)
Create an Okta API token, following instructions in Okta help. You will add the token to the SumoJanus properties file, later in this procedure.
Step 2: Download the SumoJanus package (DEPRECATED)
The following SumoJanus file is required to collect logs from Okta. Download the appropriate file for your system.
| Linux | Windows | |
|---|---|---|
| SumoJanus v3.0.1 package file | sumojanus-okta-dist.1.0.2.tar.gz | sumojanus-okta-dist.1.0.2.zip |
Step 3: Deploy the SumoJanus package (DEPRECATED)
If you have not previously set up SumoJanus, follow the steps in New SumoJanus installation. If you have previously set up SumoJanus, follow the instructions in SumoJanus installation update.
New SumoJanus installation
Copy the package file you downloaded in Step 2 to the appropriate sumojanus folder, then unzip them there.
- On Linux, run the following command:
- On Windows, you can use Windows Explorer to open the zip package and copy it to the appropriate target folder.
Update your SumoJanus installation
- Backup conf/sumologic.properties and the data folder.
- Setup a New SumoJanus installation
- Migrate the backed up conf/sumologic.properties and data folder to the new Janus folder
- Modify the paths in Step 6 below to point to the new folder.
Step 4: Edit the Properties file (DEPRECATED)
- Open the file
<sumojanus_foldername>/conf/sumologic.propertiesin a text editor and add the following lines to the end of the file. You will replace the <variables> with information (including the brackets) you enter in the following steps.
- api_token. Enter the Okta API token that you created in the Generate the Okta API token step.
- okta_org_url. Enter your Okta URL. Note that the URL starts with https, and not http.
- stream_pos_path. Replace the
${path}variable with the actual path on the server where SumoJanus is installed. For example: '/home/sumojanus' - Save your changes. Your
sumojanus/conf/sumologic.propertiesfile should look similar to this example:
Step 5: Configure a Collector (DEPRECATED)
To avoid errors, use the latest bundled JRE version listed in the Collector Release Notes. Since the JRE folder can change with collector upgrades, we strongly recommend copying this JRE folder to a separate place and pointing the JAVAPATH to that folder. To check the current JRE folder the collector is using, go to the collector folder under config/wrapper.conf, and look for the variable wrapper.java.command.
Configure an Installed Collector on a Linux or Windows machine. By default the Collector will come with a Java Runtime Environment. To ensure that SumoJanus can locate Java, you may need to update the .bat or .bash file, as described below.
On Windows, update SumoJanus_Okta.bat
Navigate to the folder where you installed SumoJanus, and open SumoJanus_Okta.bat in a text editor. Line 3 of the script sets JAVAPATH to C:Program FilesSumo Logic Collectorjrebin as shown below:
set JAVAPATH='C:Program FilesSumo Logic Collectorjrebin'
If your collector JRE is in a different location, update Line 3 accordingly.
On Linux, update SumoJanus_Okta.bash
Navigate to the folder where you installed SumoJanus, and open SumoJanus_Okta.bash in a text editor. Update the script as follows:
- Add a line that sets
JAVA_HOMEto point to the location of your JRE, just before the last line of the script. For example, if your collector's JRE is in/opt/SumoCollector/jre/bin, insert this line:JAVA_HOME=/opt/SumoCollector/jre/bin The last line of the script is:
java -jar ${SUMOJANUS_JAR_FILE} ${runMode} OktaCollector-1.0.2.jar -e 1800
Prefix the line with$JAVA_HOME/, like this:$JAVA_HOME/java -jar ${SUMOJANUS_JAR_FILE} ${runMode} OktaCollector-1.0.2.jar -e 1800
Step 6: Configure a Source (DEPRECATED)
For guidance creating your Source Category naming convention, see Best Practices: Good Source Category, Bad Source Category.
To configure a Script Source, do the following:
Configure a Script Source. Collectors using version 19.245-4 and later do not allow Script Sources to run by default.
To allow Script Sources you need to set the Collector parameterenableScriptSourcein user.properties to true and restart the Collector.Linux
Windows
- Configure the Source fields:
- Name. OktaCollector.
- (Optional) Description.
- Source Category. okta
- Frequency. Every 5 Minutes
- Specify a timeout for your command. Activate the checkbox and select 60 Minutes
- Command. For Linux, use
/bin/bash.For windows, use Windows Script. (Specify the correct path on your system). - Script. Use the absolute path to sumojanus that you created in the Deploy the Packages step, such as
/home/ubuntu/sumojanus/bin/SumoJanus_Okta.bash.(Do not select 'Type the script to execute.') - Working Directory.
$path/sumojanus,where $path is the absolute path of SumoJanus that you created in the Deploy the Packages step.
Click Save.
Query samples
Okta For Anyconnect
Details of Applications Deleted
_sourceCategory = 'okta' 'application.lifecycle.delete'
| json field=_raw 'eventType' as event_type
| where event_type = 'application.lifecycle.delete'
| json field=_raw 'outcome.result' as outcome_result
| json field=_raw 'displayMessage' as display_message
| json field=_raw 'published'as published_time
| json field=_raw 'actor.displayName' as okta_user_name
| json field=_raw 'actor.alternateId' as okta_user_id
| json field=_raw 'actor.type'
| json field=_raw 'severity' as severity
| json field=_raw 'target[0].displayName' as app_name
| json field=_raw 'target[0].type' as app_type
| json field=_raw 'client.ipAddress' as client_ip
| json field=_raw 'client.geographicalContext.city' as city
| json field=_raw 'client.geographicalContext.state' as state
| json field=_raw 'client.geographicalContext.country' as country
| json field=_raw 'client.geographicalContext.postalCode' as postal_code
| count by app_name, okta_user_id, outcome_result, display_message
Details of MFA Deactivate Event
Okta Anyconnect Free
_sourceCategory = 'okta' 'user.mfa.factor.deactivate'
| json field=_raw 'eventType' as event_type
| where event_type = 'user.mfa.factor.deactivate'
| json field=_raw 'outcome.result' as outcome_result
| json field=_raw 'published' as published_time
| json field=_raw 'actor.displayName' as actor
| json field=_raw 'actor.alternateId' as actor_id
| json field=_raw 'actor.type'
| json field=_raw 'severity' as severity
| json field=_raw 'client.userAgent.os' as OS
| json field=_raw 'client.userAgent.browser' as browser
| json field=_raw 'client.device' as device
| json field=_raw 'client.ipAddress' as client_ip
| json field=_raw 'client.geographicalContext.country' as country
| json field=_raw 'client.geographicalContext.state' as state
| json field=_raw 'client.geographicalContext.city' as city
| json field=_raw 'target[0].displayName' as okta_user_name
| json field=_raw 'target[0].alternateId' as okta_user_id
| count by okta_user_id, actor, outcome_result, country, state
